Search
Tamper-proof logs
Ensuring that personal data are only accessed by authorized users—and for authorized purposes—requires some method of tracking transactions and who has accessed the data and when. Automatic, tamper-proof logging of transactions involving identity data is a best-practice method for enabling both institutional and personal oversight of how these data are being used.
Any logs or audit data collected must comply with privacy and data protection requirements for the ID system in question. At a minimum, logs should be:
-
protected from unauthorized access (and have that use monitored);
-
protected from unauthorized copying or exfiltration; and
-
devoid of personal data.
In India and Estonia, for example, logs are digitally signed to detect tampering. In addition, chaining digitally signed logs in Estonia makes it difficult to change their history (see Box 23). Using emerging technologies such as blockchain may also have the potential to increase the security of these logs by making them immutable, even to the agencies that maintain them.
In addition to facilitating audits of data use, logs are of vital importance in instances of fraud or security breaches, as they will form the basis of investigations or reviews of system activity and data access. The tamper-proof nature of the logs is also crucial, as attackers who gain access to the underlying IT systems may attempt to alter or delete this information. It is therefore important to put in place systems and technologies that minimize the risk of such attack and ensure the integrity and security of audit logs, such as:
-
Ensuring that logs from application servers are removed as soon as possible and sent to a central log management system
-
If possible, sending log data directly to a centralized log management system
-
Making sure that log files and log transactions are encrypted in transit and at rest
-
Ensuring that the centralized log management system has sufficient access control and authentication as well as access audit logging
-
Applying role-based access to log file systems to ensure that only authorized personnel may perform actions such as deleting log files
-
Analyzing log file activity to identity gaps in logging or patterns of corruption which may highlight suspicious activity
|
Box 23. Tamper-proof logs in Estonia Estonia’s Personal Data Usage Monitor (open source software) filters and logs transactions containing personal data. It is used at the exit points of information systems from where the data flows to other systems. This independent software can capture transactions containing personal data based on rules defined to identify personal data in data traffic flowing out of a system and log them with timestamp and digital signature. As shown in the figure below, an “extractor” component creates a record each time a resident’s data is accessed, which contains metadata about usage. A “logger” component logs this event in time-stamped, digitally signed tamper proof logs. The system/database owners cannot choose which transactions to log or hide/delete transactions. 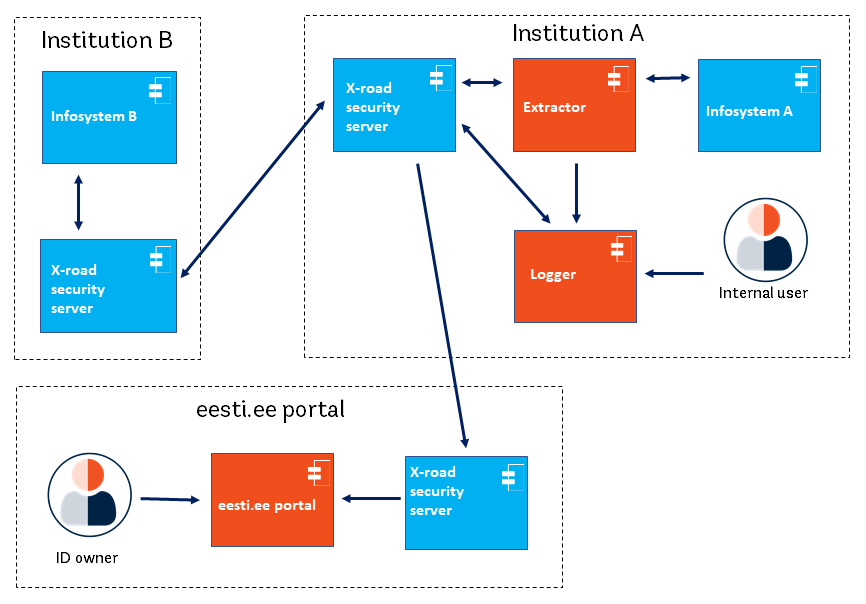
These logs are then accessible to the users via the citizen portal (see Box 22), offering a comprehensive view of how personal data has been used by the government (and the opportunity to contest in the case of misuse). Internal system users also check the logs to monitor the activity and flag anomalous behavior for preventive and corrective measures. Source: Privacy by Design: Current Practices in Estonia, India, and Austria. |
