Search
ID 101: Basic concepts
“Identity” and “identification” can mean different things in different contexts. For the purposes of this Guide, identity refers to the combination of characteristics or attributes that make a person unique in a given context. While there are limitless personal attributes that are inherent to, chosen by, or ascribed to a person that make them unique, the particular attributes most relevant in this context include core biographic data (e.g., name, age, address) and certain biometric features (e.g., a facial image, fingerprints, iris scans).
ID systems collect and validate identity attributes in order to establish a person’s identity and provide proof of that identity in the form of a credential (e.g., unique ID number, card, certificate, mobile ID, etc.). These credentials can be use by the person through some method of authentication to “assert” or prove their identity to third, “relying” parties—e.g., government agencies, financial institutions, employers, etc.—that require some assurance of who they are.
Figure 3. The basic roles of ID systems
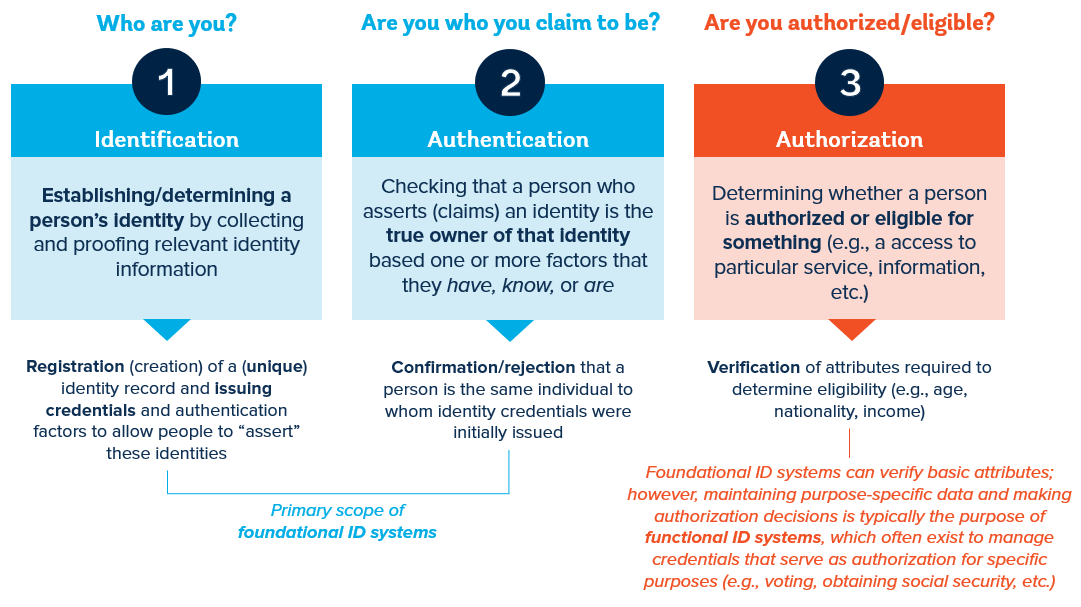
As summarized in Figure 3, ID systems and personal attributes can help answer one or more of the following questions:
-
“Who are you?”
-
“Are you who you claim to be?”
-
“Are you authorized or eligible for something?”
As described in Section I. Why ID matters for development, these three questions are fundamental to service delivery and the fulfillment of rights and obligations. Both public and private sector institutions need to know who people are (question 1) and be able to trust that they are “really themselves” overtime—i.e., that no one has stolen or hacked their identity credentials (question 2)—as a part of many basic economic, social, political, and digital transactions. Furthermore, relying parties (e.g., service providers) may need to confirm—either during initial onboarding of a new beneficiary or client, or on an ongoing basis—that the person is eligible to access a particular right, service, information, or system functionality (question 3). Such determinations often require the ability to verify specific attributes about a person against a trusted source of information (e.g., a person’s age, income level, occupation, etc.).
In some cases, the same ID system used for identification and authentication may be able to provide the information needed for authorization or eligibility determination. In many other cases, however, relying parties must maintain or access additional information that is beyond the scope of the ID system itself. For example, a social service agency may rely on a person’s government-recognized digital ID to identify and authenticate a new beneficiary, ensuring that they really are the person that they claim to be. In order to determine whether the person is eligible for a specific safety net program, however, the agency may also need to verify a person’s income against a different trusted source of information (e.g., a tax register) to determine whether or not they are eligible for certain benefits.
