Search
Digital certificates and PKI
Digital certificates facilitate secure electronic communication and data exchange between people, systems, and devices online. They are issued by Certificate Authorities (CAs) and perform two primary functions:
-
Verifying the identity of the sender/receiver of an electronic message
-
Providing the means to encrypt/decrypt messages between sender and receiver (i.e., binding and entity to their public key)
There are three basic types of digital signature certificates:
-
Individual digital signature certificates (signing certificates): These certificates are used to identify a person and include personal information. They can be used to sign electronic documents (i.e., to provide electronic signatures) and emails, and to implement access control mechanisms for sensitive or valuable information.
-
Server certificates: These certificates identify a server (computer) and contain the host name or IP address. They are used for one- or two-layer SSL to ensure secure communication of data over a network.
-
Encryption certificates: These certificates are used to encrypt a message using the public key of the recipient to ensure data confidentiality during transmission. Different signatures for encryption and digital signatures are available from different CAs. (adapted from Government of India 2010)
Figure 13. Digital certificates
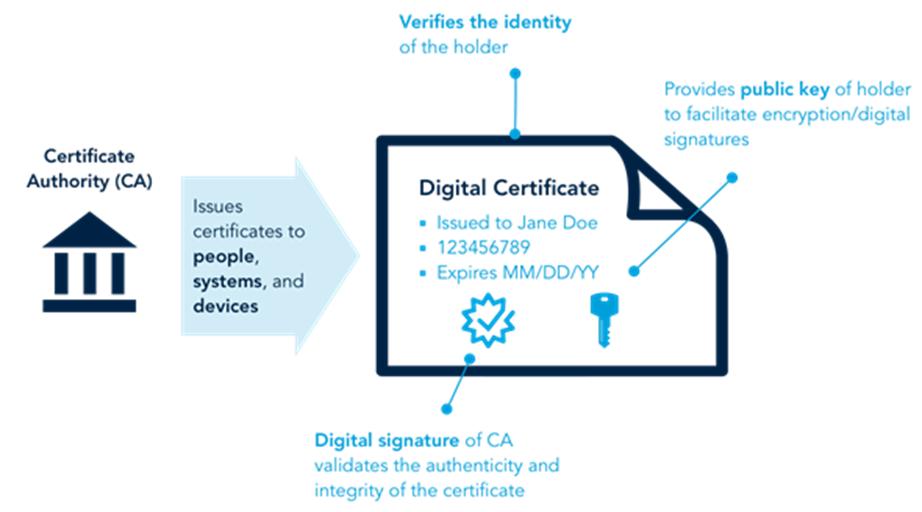
A system—including policies, institutions, and technologies—that manages the distribution, authentication, and revocation of digital certificates is often referred to as public-key infrastructure (PKI). Because digital certificates are standard in data exchange and security protocols for digital ID systems (including the TLS encryption measures described above, as well as smartcard- and mobile-based authentication), a country’s PKI is landscape is a common building block for many ID systems.
For example, when a smartcard or SIM card that uses PKI for authentication and digital signatures is personalized, it is issued with a private key and digital certificate signed by a CA that attests to the authenticity of the credential and provides the public-key necessary for other devices (e.g., card readers, servers, etc.) to verify the authenticity and integrity of the card.
While it is possible for an ID provider to create its own digital certificates, it is often more practical and reliable to use a trusted third party as the CA and/or Root Certificate Authority. Future versions of this Guide will include a deeper description of various options for setting up a PKI infrastructure, as well as alternatives.
