Search
Encryption
In any ID system, personal data is vulnerable to being accessed or intercepted and read by unauthorized actors during storage and when it is transferred. This includes when data is hosted in data centers or the cloud, and in particular during transactions that involve online authentication, verification, or exchange of identity data. For example, the majority of physical network links provide poor confidentiality and privacy for transmitted data, particularly where data must pass through the open internet. Although this may be convenient and efficient for users and administrators, it also leads to vulnerabilities that may expose personal data to a variety of attacks by eavesdroppers.
|
Box 19. Understanding public-key encryption and digital signatures Encryption is the process of encoding information by inputting it—together with another parameter or “key”—into an encryption algorithm or “cipher.” There are two basic methods of encryption for securing data transmission:
In public-key encryption, a pair of keys are generated for an entity—a person, system, or device—and that entity holds the private key securely, while freely distributing the public key to other entities. Anyone with the public key can then use it to encrypt a message to send to the private-key holder, knowing that only they will be able to open it (see figure below). 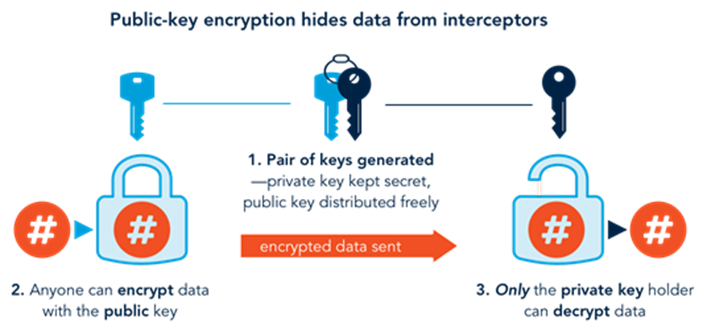
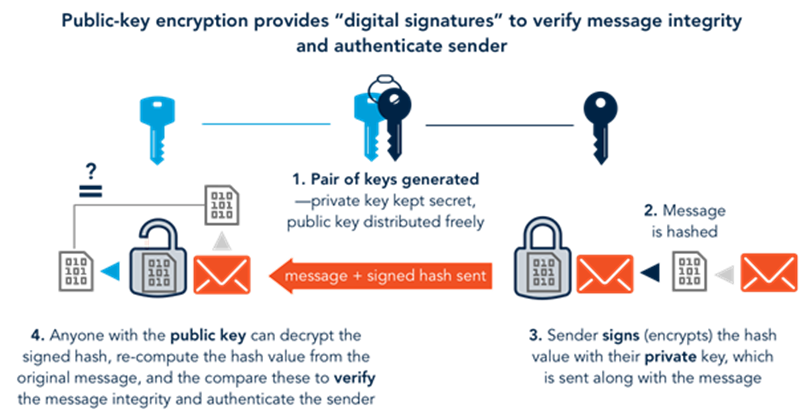
In addition, asymmetric encryption is used for digital signatures. Here, the message (i.e., data) is “signed” by the private key, and the recipient of the message can then use the sender’s public key to verify its integrity, ensuring that it came from the private-key holder and was not tampered with in transit (see figure below).
|
Cryptographic methods are the most effective and commonly used tools for protecting data during storage and transactions. Specifically, both symmetric and asymmetric encryption (see Box 19) help protect the confidentiality and security of personal information by:
-
Hiding data: Encrypted data are “locked” and cannot be read or understood by an interceptor or unauthorized user, except through a brute force attack that requires significant computing resources.
-
Sealing and authenticating data: The use of asymmetric or public-key encryption allows senders to “digitally sign” a message or data so that the receiver can be sure that the sender is who they claim to be, and that the message was not tampered with during transit.
Given these functions, encryption plays multiple roles in ID systems, as shown in Table 22.
Table 22. Example requirements for data encryption in an identity system
| Requirement | Description |
|---|---|
|
Message Confidentiality |
Encryption can prevent the interception and reading of messages in transit either at the user agent (e.g., a web browser) or in transit between trusted entities. |
|
Message integrity |
Ensuring the integrity of a message—i.e., that it was not altered during transmission—is often accomplished through the addition of a digital signature using public-key encryption. |
|
Replay Protection |
Encryption such as Secure Sockets Layer (SSL) can prevent “replay” attacks on authentication requests and responses. Other methods of replay protection include using public-key encryption to sign messages and setting a validity period for the message coupled with message request identifier tracking. |
|
Transport Layer Protection |
As a baseline all computer-to-computer communication should utilize the latest version of Transport Layer Security (TLS) as advised by national technical advisory bodies. |
|
Eco-system Technical Trust |
Authentication of entities in an ID federation based on cryptographic proof to ensure that only entities that are legitimate members are able to interoperate with the technical components of the federation scheme (e.g. identity providers, attribute providers, relying parties etc.). |
Encryption technologies provide strong confidentiality protections but only for as long as the private keys used to ensure this protection remain secret. Therefore, key management is extremely important. These secret keys are a prime target for organized crime and other attackers as they effectively open access to the most valuable data held by organizations. It should also be noted that the methods of obtaining these keys are not restricted to technological means and often center on the identification of vulnerable targets for extortion, theft, coercion, and confidence tricks (e.g., phishing).
To minimize the possibility of data loss due to keys being compromised, steps should be taken to regularly rotate keys. This approach reduces the risk of data loss due to a key being compromised as any stolen keys will become useless at regular intervals and have a reduced scope for attack. For example, an automatic key rotation scheme such as Forward Secrecy ensures that a new set of keys are used for each communication session, and key are discarded once the session has ended. This means that sensitive data cannot be recovered and decrypted after the transmission has ended as the keys are no longer available. For this reason, it is recommended that no long-term secrets (keys) are used to protect the confidentiality of interactive end-to-end conversations in digital ID systems.