Search
Types of credentials and authenticators
A credential can be defined as any document, object, or data structure that vouches for the identity of a person through some method of trust and authentication. Simply put, a credential is the thing that a person presents—in person or remotely—to say “this is who I am.” The types of credentials issued in an ID system vary along multiple dimensions, including whether or not they are physical (i.e., they must be physically carried by a person in order to use them), and whether or not they are digital (i.e., they are machine readable and therefore can be used in a digital environment). In addition to credentials themselves, the authentication process may involve presenting the credential along with additional factors (i.e., “authenticators”) that bind the person to the credential, offering assurance that the person in possession of the credential is its rightful owner. Common types of credentials and authenticators are shown in Figure 27.
Figure 27. Examples of credentials and authenticators commonly issued by foundational ID systems
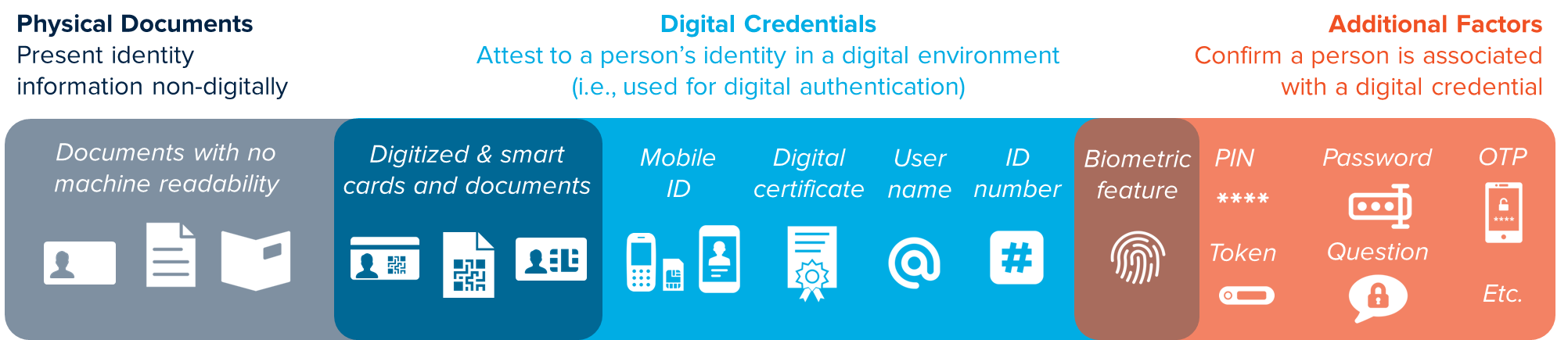
Credentials vary in terms of format and functionality—e.g., the medium in which identity data are stored and their ability to be used for authentication in multiple environments—as well as the levels of security they provide and their cost. Historically, most countries have used physical documents such as national ID cards and birth certificates as the basis for their foundational ID systems. Advances in digital technology have led to the digitization of physical credentials that now include magstripes, barcodes, and/or chips that allow them to be used in a digital environment.
As societies become more digital, we have begun to see a move toward digital-only ID systems that do not rely on the possession of a physical credential. Such approaches use credentials that are stored only on computers, mobile devices, and servers—or in the form of user names and ID numbers—and which rely on biometrics and other factors for authentication. In the UK, for example—where people already have a variety of physical documents to prove who they are for in-person transactions—the GOV.UK Verify system provides digital-only ID credentials that allow end-users to authenticate themselves remotely via multiple factors (e.g., a username and password + mobile authenticator) for online services. The BankID systems in Sweden and Norway provide similar “layers” of digital authentication for e-services that do not rely on physical credentials.
However, there are certain limitations to the use of digital-only approach to credentials and authentication. In India, for example, the Aadhaar system allows people to authenticate themselves for in-person and remote transactions with only their unique ID number (called “UID”) and a fingerprint or one-time password (OTP). However, authentication through this method—i.e., with no physical credential—requires connectivity to a database, which may not be feasible in countries with unreliable or uneven internet or mobile coverage, although these gaps are narrowing over time. In addition to the connectivity concern, experience suggests that in many contexts, people may prefer physical credentials as they are more intuitive or easier to use and/or hold a symbolic value. In India, for example, many people still carry the Aadhaar “card” (a paper receipt with UID printed on it) in order to avoid remembering the 12-digit number (IDinsight 2018). The viability of the ID-number-as-credential option therefore requires careful consideration of the country context and public consultations to better understand people’s preferences.
As with other topics discussed in this Guide, the choice of credentials should be based on multi-stakeholder consultations and user-centric design considerations that reflect the overall vision and use-cases for the ID system, as well as costs and other context-based constraints. For example, areas with low-connectivity and high levels of fraud may require physical credentials that can be securely authenticated in an offline-environment. Where internet connectivity and/or mobile phones are widespread, virtual credentials may be more feasible as a primary tool for authentication.
Ideally, the ID system should allow for easy adoption of multiple credential technologies, including new technologies that may emerge in the future. Through the use of open standards and procurement practices that avoid vendor and technology lock-in, practitioners can ensure that the system is able to adapt and take advantage of new solutions. In addition, a number of ID systems issue multiple types of (optional) credentials, as discussed in Box 34. Giving people choice over their credentials will increase convenience and nurture innovation around ID services.
|
Box 34. Examples of multiple types of credentials in one country ID credentials may take multiple forms within a single country. In Austria, for example, the national ID can be issued as a physical “citizen card” (Bürgerkarte) or a virtual mobile ID (Handy-Signatur). Both can be used for digital authentication and e-signatures. For more information, see https://www.buergerkarte.at/en/. In Estonia, people with the standard national ID smartcard (ID-card) can also apply for a supplementary smartcard called “Digi-ID,” which provides the same functionality (digital authentication and e-signatures) but does not include a photo of the person and therefor is intended only for non-face-to-face transactions. Estonia also offers two types of mobile ID for digital authentication, e-signatures and access to online services: one, called “Mobiil-ID”, leverages PKI-based SIM technology and is offered by Estonian mobile companies; the other, called “Smart-ID”, is an app that can be downloaded on any smartphone. For more information, see https://www.id.ee/. Source: Adapted from the ID Enabling Environment Assessment (IDEEA). |
The remainder of this section focuses on important issues related to three of the most common types of credentials used in foundational ID systems: ID numbers, cards, and mobile IDs.
