Search
10.12.3 Levels of assurance frameworks
A “level of (identity) assurance” is the certainty with which a claim to a particular identity made by some person or entity can be trusted to actually be the claimant's “true” identity (WB-GSMA-SIA 2016). Higher levels of assurance reduce the risk of a fraudulent identity and increase the security of transactions.
Assurance levels depend on the strength of the identity proofing process and the types of credentials and authentication mechanisms used during a transaction. For identity proofing, the level of assurance depends on the method of identification (e.g., in-person vs. remote), the attributes collected, and the degree of certainty with which those attributes are verified (e.g., through cross-checks and deduplication). For authentication, the level of assurance depends on the type of credential(s), the number of authentication factors used (i.e., one vs. multiple), and the cryptographic strength of the transaction.
Figure 30. ISO and eIDAS levels of assurance
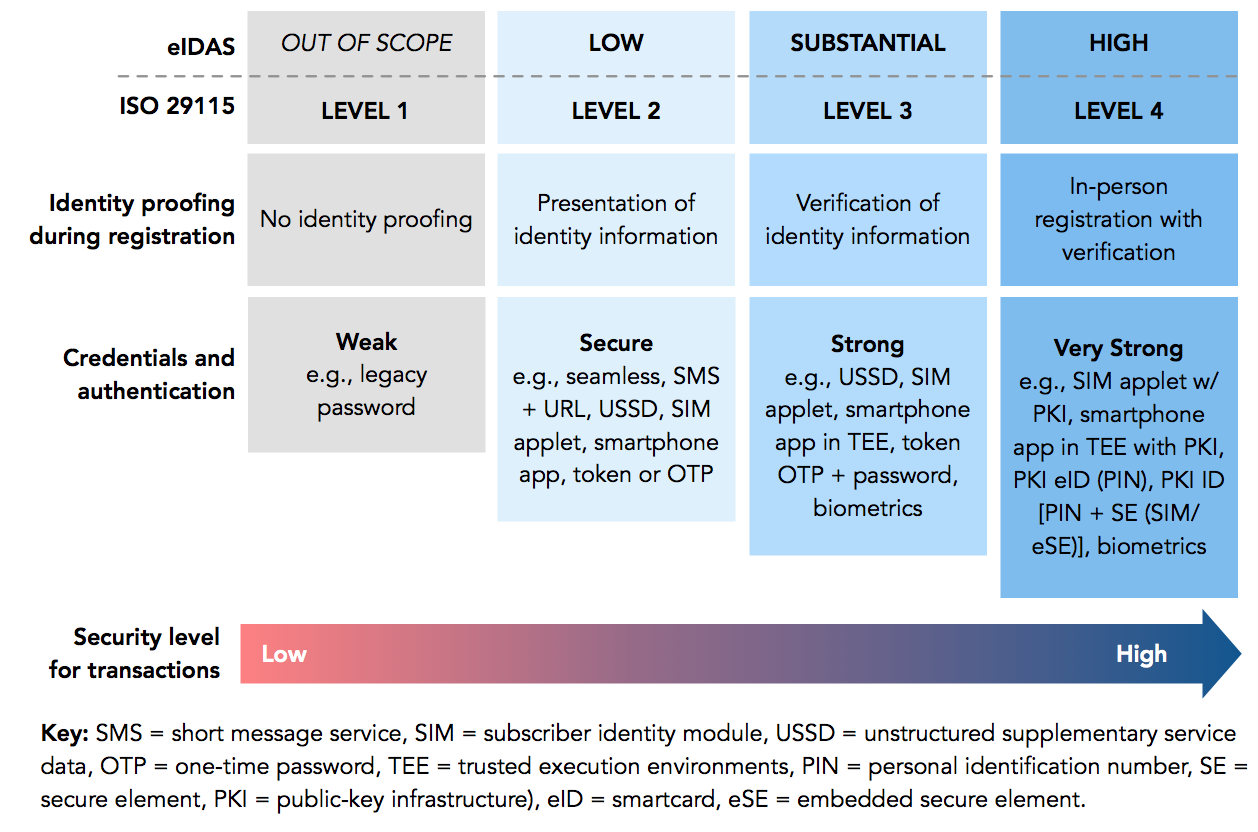
Source: Adapted from Digital Identity: Public and Private Sector Cooperation
Both eIDAS and ISO/IEC 29115 have developed standards, shown in Figure 30, to classify levels of assurance based on these processes and technologies.14 In addition, recent guidelines from the National Institute of Standards and Technology (NIST) have adapted this framework to separate out assurance levels for identity proofing (“identity assurance level,” or IAL) and for authentication (“authenticator assurance level,” or AAL), as shown in Box 44. In addition, the NIST framework distinguishes levels of assurance for the assertion of identity in a federated environment (“federated assurance level”, or FAL). While many systems will have the same level for each, practitioners can also select IAL, AAL, and FALs as distinct options, depending on the system requirements.
|
Box 44. NIST levels of assurance for digital ID Identity proofing LOAs:
Authentication LOAs:
Federation LOAs:
Source: NIST Digital Identity Guidelines (Special Publication 800-63-3) |
The LOAs selected depend on the use case; some sectors and types of transactions will require higher levels of assurance than others. For example, changing an address may rely on a lower level of assurance than changing a password. Financial and health services often require a higher level of assurance than others due to the sensitivity of the data that is collected and maintained in those systems. Ideally, the ID system’s authentication architecture will be able to provide multiple levels of assurance appropriate to different use cases.
The selection of LOAs—and the identity proofing processes, the types of credentials, and authentication mechanisms that enable them—should be based on a number of factors. including:
-
The likelihood of a failure, breach, or unauthorized release of sensitive information
-
The risk to individuals, institutions, programs, public interest if a failure or breach occurs—i.e., based on the level of sensitivity of the service/information and the expected level of harm
-
The convenience and inclusivity of the identity proofing and authentication processes, as higher LOAs could increase the likelihood of exclusion errors.
LOAs are particularly important for federation and mutual recognition across borders, where an ID system must meet a particular level of assurance in order to qualify for recognition for a given purpose.
